Why Container Isolation Isn't Optional: Lessons from RediShell
Today, Wiz Research disclosed CVE-2025-49844, dubbed RediShell, a critical 10.0 CVSS vulnerability in Redis that enables full remote code execution on the host system. The vulnerability exploits a 13-year-old use-after-free bug that allows attackers to escape Redis's Lua sandbox and execute arbitrary code. While the technical details are concerning enough, what makes this vulnerability particularly alarming is how it intersects with modern container deployment practices.
With an estimated 330,000 Redis instances exposed to the internet and 57% of cloud environments running Redis as containerized workloads, we're looking at a massive attack surface where any internet-connected attacker can compromise not just Redis, but the entire host system.
This isn't Redis-specific – it's a container security problem. The real issue is weak container isolation. Had proper isolation been implemented, this vulnerability would be trivial.
The Container Security Illusion: Why Namespaces Fail
The container ecosystem has revolutionized application deployment, but it's built on a foundation that was never designed to be a security boundary. Traditional containers are essentially standard Linux processes wrapped in namespaces and cgroups. While these primitives provide resource isolation and process separation, they were never intended to contain adversarial code or prevent privilege escalation.
There’s a widely known but uncomfortable truth in modern cloud architecture: namespaces are not security boundaries.
When you run a container using Docker, containerd, or any traditional container runtime, that container shares the host kernel. Every system call from your containerized application goes directly to the same kernel that's managing your host system and every other container. A vulnerability that allows kernel exploitation – like CVE-2025-49844's RCE capability – gives an attacker a direct path from the container to the host.
Even with strict sandboxing techniques like seccomp profiles, AppArmor, and SELinux policies, you're playing defense against an ever-growing attack surface. These security layers can be effective when implemented perfectly, but "perfect" is a high bar in complex production environments. A single misconfiguration, a single bypass technique, and the entire security model collapses.
Why RediShell Is a Wake-Up Call for Container Security
This Redis vulnerability perfectly illustrates the container isolation problem:
Post-authentication attack that becomes pre-authentication in practice. The vulnerability requires authentication, but the official Redis container image ships without authentication enabled. This means that in many real-world deployments, there's no authentication barrier at all.
Widespread deployment in critical infrastructure. Redis is deployed in approximately 75% of cloud environments for caching, session management, and pub/sub messaging. It's everywhere, and much of it is containerized.
Direct path from container to host. Once the attacker achieves RCE within the Redis container, they have full access to the host system. They can exfiltrate SSH keys, steal IAM tokens and certificates, install malware, and move laterally across your infrastructure.
The attack chain is straightforward: exploit Redis → escape Lua sandbox → execute code in container → exploit shared kernel → compromise host. Traditional containerization does nothing to prevent this progression.
Edera Zones: Hardware-Enforced Isolation for Containers
Edera takes a fundamentally different approach to container security by recognizing that true isolation requires a hardware-enforced security boundary. Instead of running containers as processes on a shared kernel, Edera runs each container inside a lightweight MicroVM, called Edera zones, powered by the Xen hypervisor.
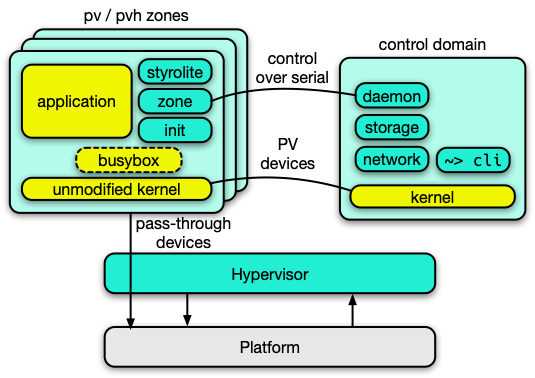
This architectural shift changes everything:
Hardware-enforced isolation. Each container runs with its own kernel inside a zone that's isolated by the hypervisor. A compromised container cannot access the host kernel or other containers because the hypervisor enforces isolation at the CPU level.
Complete mitigation of CVE-2025-49844. Even if an attacker successfully exploits the Redis vulnerability and achieves RCE within the container, they're still trapped inside the Edera zone. The vulnerable Redis instance is fully isolated from the host system. There is no shared kernel to exploit, no privilege escalation path to the host, no lateral movement to adjacent containerized workloads, and no access to secrets within containers.
Protection against future vulnerabilities. This isn't about patching one specific CVE—it's about architectural immunity to an entire class of attacks. Whether it's CVE-2025-49844 or the next critical vulnerability in Redis, PostgreSQL, nginx, or any other widely deployed software, Edera's isolation model prevents container-to-host breakout.
.png)
The Multitenancy Problem in Shared-Kernel Containers
The shared kernel model becomes even more problematic in multitenant environments, which describes virtually every modern container deployment. When you're running dozens or hundreds of containerized workloads on the same host, you're creating an environment where a single compromised container can potentially impact everything else on that system.
Consider the typical scenario: you have multiple microservices, third-party dependencies, and maybe even containers running code from external customers. All of these are sharing the same kernel. A vulnerability in any one of them becomes a vulnerability in all of them.
Edera eliminates the shared fate of container security. Each container runs in its own isolated zone with its own kernel. A compromised Redis container can't affect your API gateway. A vulnerability in a third-party logging agent can't escalate to your database. The isolation is complete and absolute.
The Reality of Modern Threats: Why Shared Kernels Put You at Risk
CVE-2025-49844 is notable for its 10.0 CVSS score – only about 300 vulnerabilities received that rating in the past year. But here's the sobering reality: this won't be the last critical vulnerability in widely deployed open-source infrastructure. Redis has maintained an excellent security track record for years, and this vulnerability still emerged from a 13-year-old bug.
The supply chain we depend on – the open-source databases, web servers, message queues, and caching layers that power modern applications – will continue to have vulnerabilities. That's not a criticism; it's an acknowledgment that software is complex and bugs are inevitable. What matters is how your architecture responds when a vulnerability is discovered and exploited.
Traditional containers offer you a choice: patch immediately and hope you catch every instance, or accept the risk of compromise and potential host-level access. Neither option is acceptable for critical infrastructure.
Edera offers a third path: true isolation that contains the blast radius of any vulnerability. Patch on your schedule, not an attacker's, knowing that even an actively exploited vulnerability can't break out of its Edera zone.
Isolation Isn't Optional – It’s the Future of Secure Containers
The container revolution brought us unprecedented deployment flexibility and developer velocity. But we've been accepting a security tradeoff that doesn't need to exist. Traditional container isolation was built for resource management and process separation, not for containing sophisticated exploits and preventing privilege escalation.
RediShell is a stark reminder that the stakes are real. With hundreds of thousands of potentially vulnerable instances, many running without authentication in containerized environments that provide no meaningful isolation from the host, we're one RCE exploit away from widespread compromise.
The only reliable solution is true isolation—running containers in Edera zones with hardware-enforced security boundaries. Edera provides that isolation without sacrificing the performance and operational simplicity that made containers attractive in the first place.
Container isolation isn't a nice-to-have security feature. It's not something you add later or implement "when you have time." It's the architectural foundation that determines whether a vulnerability in one container remains contained or becomes a breach of your entire infrastructure.
The question isn't whether you'll face another critical vulnerability in your container workloads. The question is whether your architecture will contain it when you do.
FAQs
What makes RediShell (CVE-2025-49844) so dangerous?
It allows full remote code execution from Redis containers to the host through a shared kernel vulnerability.
Why can’t traditional container isolation stop RediShell?
Because namespaces and cgroups aren’t true security boundaries—they share the host kernel.
How does Edera prevent container escapes?
Edera runs each container in a hardware-isolated microVM (Edera zone) with its own kernel, eliminating shared-kernel exposure.
-3.png)