Security Without Sacrifice: Edera Performance Benchmarking
Container security often comes with a performance penalty—but does it have to? Edera Protect challenges this assumption by providing strong workload isolation using a container-native hypervisor that gives each container its own kernel, while maintaining performance comparable to native containers. In this technical analysis, we benchmark Edera Protect against industry alternatives including Docker, gVisor, Kata Containers, and Firecracker to demonstrate how our technology delivers security without compromising performance.
Key Findings
- Memory Performance: Edera Protect outperforms all competitors in memory operations, with performance matching or exceeding Docker in most tests
- CPU Efficiency: On par with Docker for computational workloads, significantly outperforming isolation-focused alternatives like gVisor
- System Call Performance: In paravirtualized hypervisor virtual-machine (PVH) mode, Edera exceeds even Docker's native performance
- Real-World Workloads: Only 5% performance difference compared to Docker when building the Linux kernel, while outperforming other secure alternatives by 50+%
Methodology
We conducted comparative benchmarks on an Optimistic Virtual Machine (OVM) with hardware virtualization extensions. For each platform, we created identical testing environments and ran each benchmark five times, reporting average values. Our comparison includes:
- Docker with runc (baseline for native container performance without isolation)
- Edera Protect (our hypervisor-based isolation solution)
- gVisor (Google's userspace kernel container runtime)
- Kata Containers (with Dragonball/KVM hypervisor)
- Firecracker (using firecracker-containerd runtime on Firecracker/KVM)
Performance Analysis
Memory Performance
Memory operations are critical for many workloads, especially for real-time analytics and video processing, and Edera Protect demonstrates exceptional performance in this area.
The graph shows memory throughput in GB/s across four tests. Edera Protect achieves the highest performance in sysbench read (93.8 GB/s), sysbench write (47.2 GB/s), and memcpy (23.1 GB/s) operations. For memset operations, Edera is only 1.1% behind Docker, while significantly outperforming gVisor and Kata Containers.
These results demonstrate that Edera's virtualization approach maintains near-native memory performance while adding strong isolation. gVisor shows the poorest memory performance across all tests, reflecting the overhead of its userspace kernel approach.
Note: Firecracker data was omitted from this graph as firecracker-containerd doesn't support the manual memory allocations required by these benchmarks. In tests with lower memory requirements, Firecracker performed within 2% of Docker.
CPU Performance
For computational workloads, Edera Protect maintains competitive performance comparable to Docker.
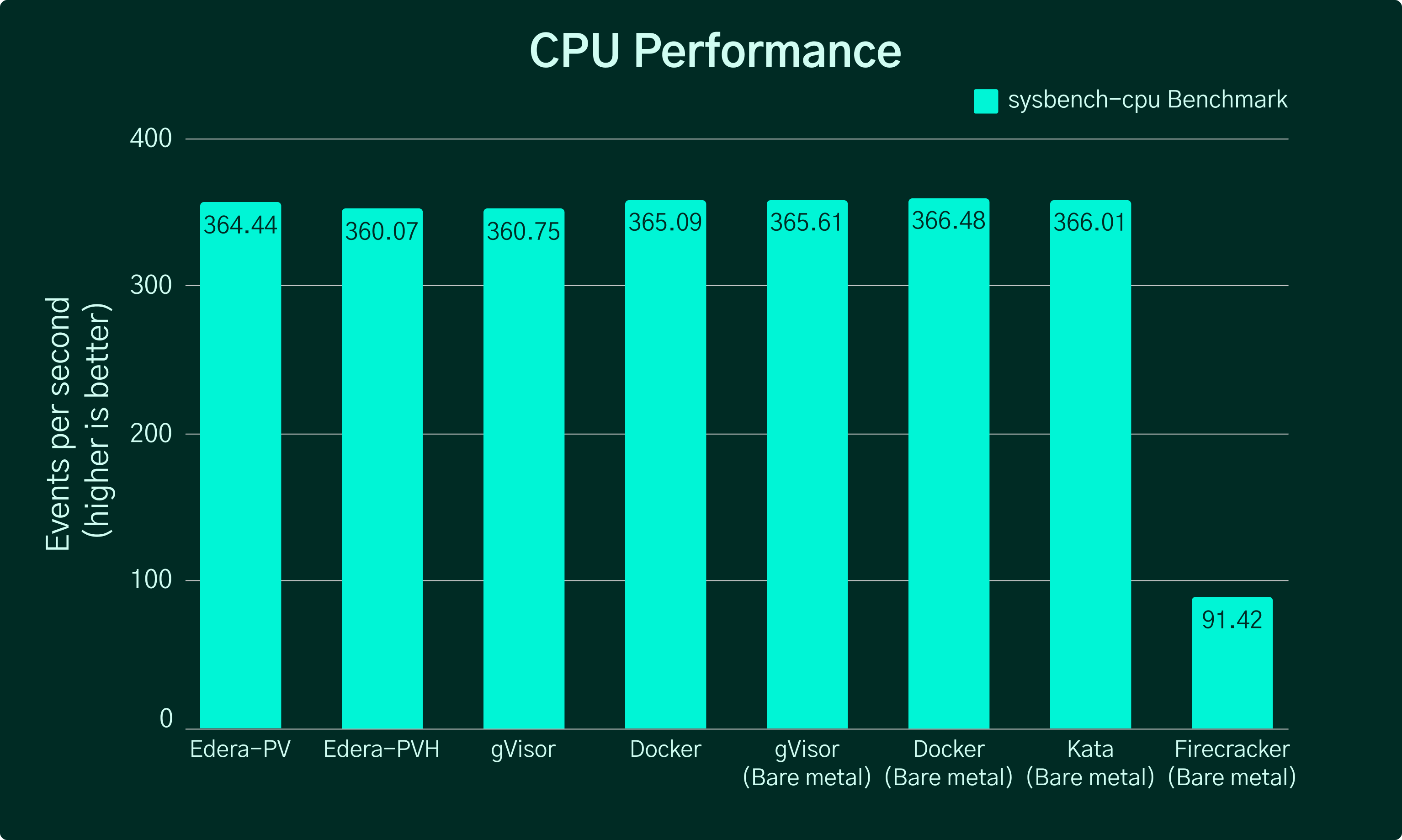
This benchmark measures CPU performance using sysbench's prime number calculation test (checking primes up to 150,000) over 4 threads, reported in events per second. The results show:
- Docker and Edera Protect deliver nearly identical performance
- Kata Containers follows closely behind
- gVisor shows moderate performance degradation
- Firecracker demonstrates significant performance limitations, likely due to thread utilization issues
The negligible difference between Edera and Docker (less than 1%) confirms that our isolation approach adds virtually no computational overhead.
System Call Performance
System calls are particularly important for isolation technologies, as they represent the boundary between container and host.
.png)
This graph compares operations per second across three common system calls. The results reveal:
- In standard mode, Edera shows moderate overhead compared to Docker (fork is 41.8% slower)
- With PVH mode enabled, Edera actually outperforms Docker across system calls
- gVisor consistently shows the poorest performance due to its security-focused interception approach
- Kata and Firecracker perform well by leveraging virtualization extensions similar to Edera's PVH mode
These results highlight a key advantage of Edera's flexible architecture: the ability to enable PVH mode when system call performance is critical, delivering both security and performance.
Real-World Performance: Linux Kernel Build
Synthetic benchmarks provide valuable comparison points, but real-world workloads offer the most practical assessment of performance impact.
.png)
This benchmark uses kcbench to measure Linux kernel build performance. The results demonstrate:
- Docker (without isolation) achieves the highest performance at 10.4 builds per hour
- Edera Protect follows closely at 9.9 builds per hour (only 5% slower)
- Edera outperforms gVisor by 59% and Kata by 52%
This real-world test confirms that Edera's isolation technology introduces minimal overhead for complex, mixed workloads combining CPU, memory, and I/O operations. The 5% difference from Docker represents a minimal tradeoff for the substantial security benefits.
Note: Similar to the memory benchmarks, Firecracker is omitted as firecracker-containerd doesn't support allocating sufficient memory for this benchmark.
Container Startup Time
For completeness, we measured container startup times, an important factor for dynamic scaling scenarios.
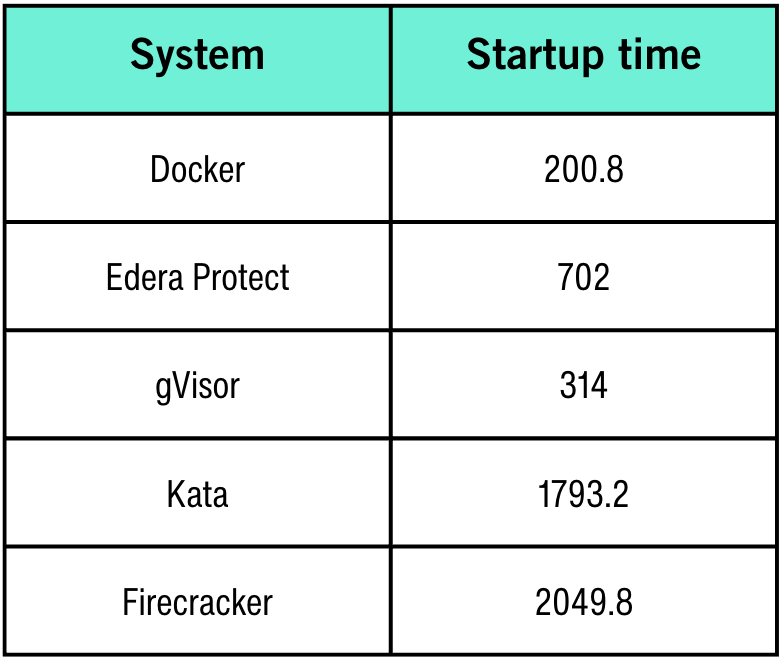
While Edera's startup time is longer than Docker's, it significantly outperforms other hypervisor-based approaches like Kata and Firecracker. Furthermore, Edera's architecture allows for dynamic resource allocation, enabling containers to be pre-provisioned with minimal resources and scaled up on demand, effectively mitigating this startup cost in production environments.
Security Without Compromise
Our benchmark results clearly demonstrate that Edera Protect delivers the security benefits of strong container isolation without the typical performance penalties:
- Memory and CPU performance comparable to or better than Docker
- System call performance that exceeds Docker when using PVH mode
- Real-world workload performance with only minimal overhead (5%)
Unlike other secure container solutions that impose significant performance penalties, Edera Protect achieves isolation without compromise. By consistently outperforming gVisor and matching or exceeding the performance of Kata Containers and Firecracker, Edera Protect establishes itself as the optimal choice for organizations that need both security and performance.
For workloads where startup time is critical, Edera's dynamic resource allocation provides an elegant solution, allowing operators to maintain a pool of pre-provisioned zones – our nextgen kubernetes sandbox – ready for immediate use.
These results validate Edera Protect's architectural approach: using container-native hypervisor to provide strong isolation between containers while leveraging hardware virtualization extensions to maintain performance. The data shows that with Edera Protect, you no longer need to choose between security and performance—you can have both.
.png)
-3.png)