Finding Xen in the Chaos: Edera's Isolation Makes Chaotic Deputy Irrelevant
JFrog security researchers disclosed several critical Chaos Mesh vulnerabilities (CVE-2025-59359, CVE-2025-59360, CVE-2025-59361). Here’s what they mean—and why Edera customers are unaffected.
JFrog’s Security Research team discovered several critical vulnerabilities in Chaos Mesh, a popular open-source project that simulates a systems ability to handle a potential problem or failure happening in your cluster. These flaws, collectively dubbed "Chaotic Deputy," have been assigned several CVEs, including the high-severity CVE-2025-59359, CVE-2025-59360, and CVE-2025-59361, all of which carry a CVSS score of 9.8.
Users of Chaos-Mesh are recommended to upgrade Chaos-Mesh to the fixed version: 2.7.3, as soon as possible.
The core of the problem lies within the Chaos Controller Manager's GraphQL API. Exploiting a vulnerability in the cleanTcs and killProcesses mutations can lead to operating system command injection. This could allow an attacker to execute arbitrary commands on the underlying host operating system, potentially leading to a cluster-wide compromise. Another related vulnerability, CVE-2025-59358, with a CVSS score of 7.5, allows for a denial-of-service attack by killing processes in any Kubernetes pod.
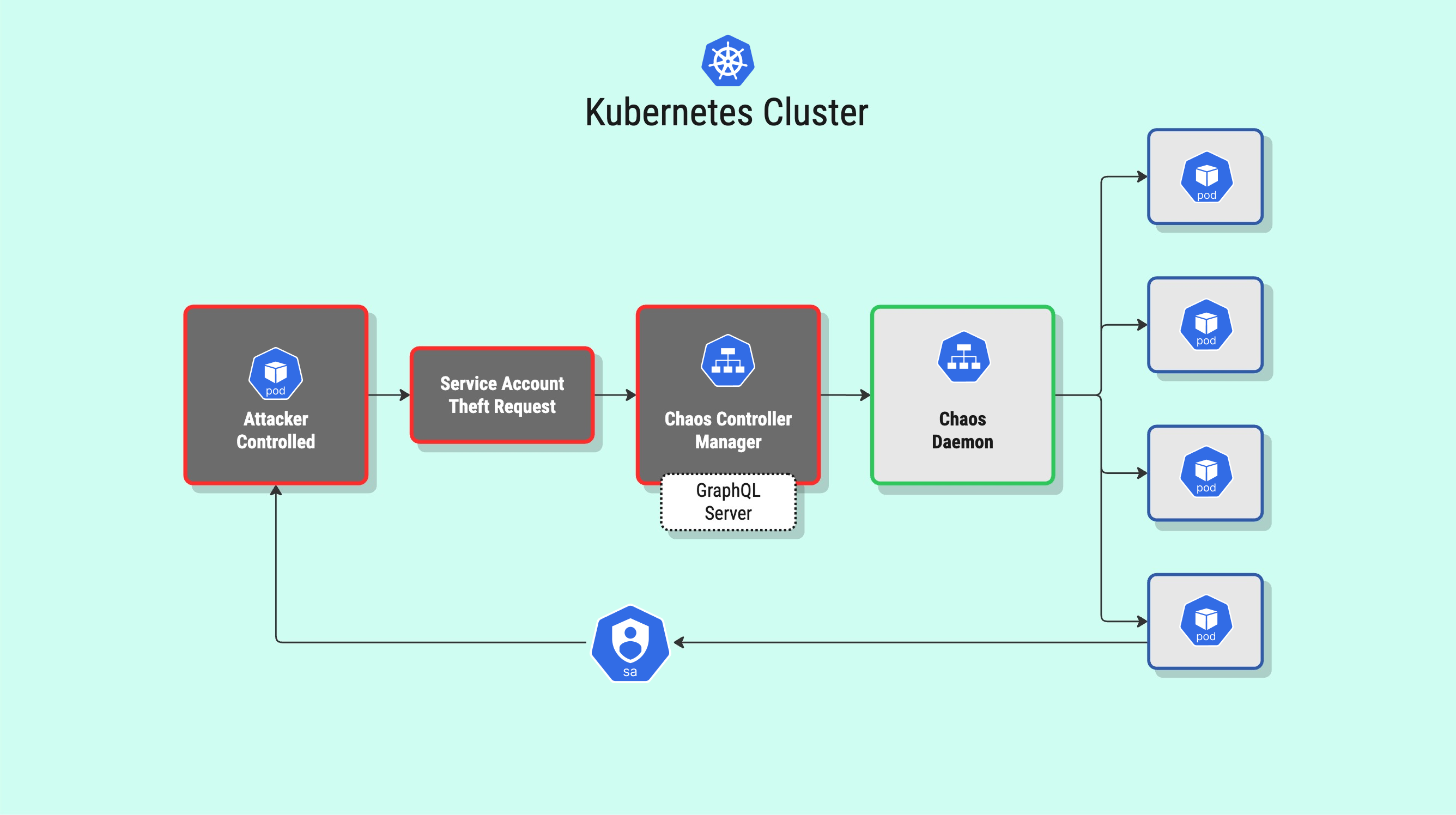
Why Chaotic Deputy CVEs Don’t Affect Edera Deployments
The good news for Edera users is that these vulnerabilities pose no threat to their deployments.
Edera's core technology is built on a fundamental security principle: the complete isolation of containers. Unlike other solutions that rely on a shared host operating system, Edera's technology ensures that each container has its own dedicated kernel and file system. This architecture eliminates the possibility of cross-container attacks and, in this specific case, prevents an attacker from using a command injection vulnerability in one container to affect the host OS or other containers.

By design, Edera's platform makes command injection attacks like the one found in Chaos Mesh impossible to execute.
This is just one of many examples of how Edera’s unique, security-first architecture provides a safer, more resilient environment for your applications. While traditional container security relies on patching individual vulnerabilities as they're discovered, Edera's, hardened runtime, provides proactive protection against entire classes of attacks.
Ready to secure your multi-tenancy environment with effortless, secure-by-design isolation? Connect with the experts at Edera today and discover how you can achieve it with just a few lines of YAML.
FAQs
What is the Chaotic Deputy vulnerability in Chaos Mesh?
A set of CVEs (CVSS up to 9.8) that allow command injection and denial-of-service in Kubernetes clusters.
Why are Edera users unaffected by these CVEs?
Edera isolates each container with its own kernel, eliminating shared-host attacks.
How does Edera differ from traditional container runtimes?
Unlike namespace-based isolation, Edera provides hypervisor-grade security without performance loss.

-3.png)