Edera and Confidential Computing: Stronger Together
Confidential computing is gaining traction for securing cloud applications—but it's often misunderstood. In this final post of our series, Edera's research team explores how our platform complements confidential computing approaches. Read all the posts in the series here.
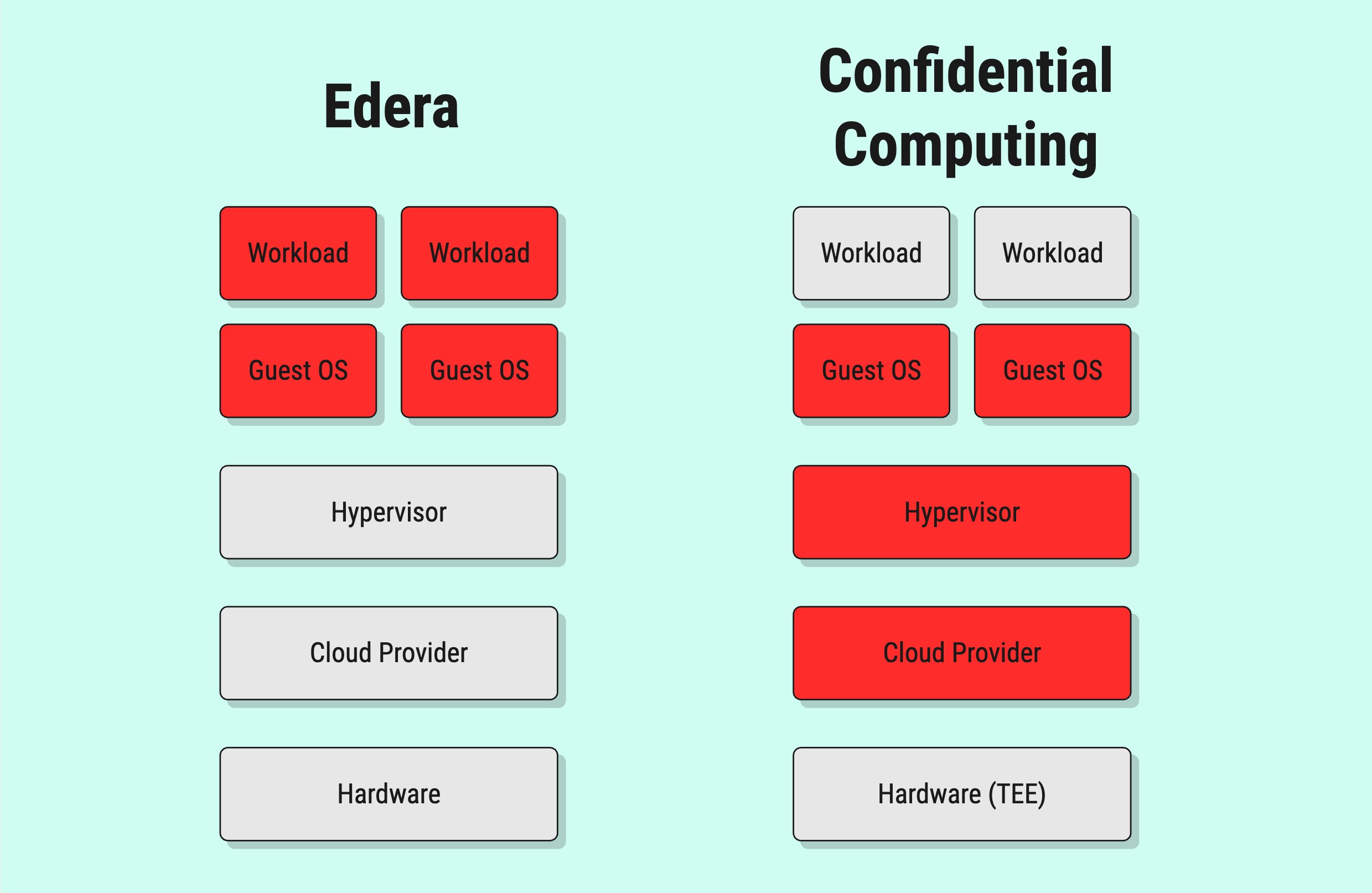
As we’ve talked about in this series, confidential computing is a powerful paradigm for securing your workloads. It provides integrity of both code and data, and encryption in use. By moving trust out of software and into a hardware trusted execution environment (TEE), it isolates applications from both other workloads and even the operating system and hypervisor.
However, there are costs associated with the adoption of confidential computing. It requires the use of specialized hardware with limits on the number of applications per TEE that make it expensive at scale. It can require re-writing applications or encountering performance limitations.This is where Edera offers a different approach.
Like confidential computing, Edera provides strong workload isolation. However, it does this through the use of hypervisor isolation without requiring specialized hardware (or even access to hardware virtualization). While this requires trust in the hypervisor rather than a hardware component, it provides good performance and compatibility with popular frameworks like Kubernetes.
Confidential Computing vs. Edera: Threat Models Explained
A key difference between Edera and confidential computing is in their assumed threat models. Confidential computing assumes that you do not trust your cloud provider or operating system, but do trust your workload itself and the hardware. Edera assumes that you don’t trust the running workloads or other workloads on the system, but do trust the hypervisor. In other words, confidential computing isolates workloads from the hypervisor, operating system, and each other, while Edera isolates workloads from each other and the hypervisor from workloads.
Choosing the Right Isolation Approach
The fundamental question becomes: where do you expect the attack to originate—from a compromised hypervisor or from a malicious workload? In an untrusted cloud, the attacker may be in the hypervisor and you need confidential computing. In a multi-tenant environment with user interaction, the attacker may be in a workload and you need Edera.
So these technologies provide different, potentially complementary, solutions which lead to the question: what if we could get both types of protection?
When thinking about this question, we came up with 2 main options: Edera with confidential computing, or Edera with key features of confidential computing (we’ll call this Edera Confidential Core).
First, you can run Edera on a TEE with encrypted memory pages. This gives all the benefits of both Edera and confidential computing including encryption in memory and in use, isolation from the OS and hypervisor, and infrastructure that is isolated from a malicious workload. However, it also comes with the same costs as confidential computing, namely it requires specialized and trusted hardware.
But what if we could achieve many of these benefits without the hardware requirements? We propose a version of Edera with hypervisor memory encryption and support for remote attestation. The hypervisor can enforce memory encryption on page faults such that it can’t be accessed by other applications, or even the host OS. This provides similar protection to a TEE, though it places trust in the hypervisor rather than the hardware.
Edera’s Xen-based architecture already provides a small trusted computing base, making it a good candidate for this integration. In addition to memory encryption, SPIFFE identities in Edera zones can provide a hypervisor-mediated root of trust for workloads enabling features like remote attestation. This proposed system, Edera Confidential Core, provides many of the benefits of confidential computing, without the need for specialized hardware.
Comparing Confidential Computing Options with Edera and Edera Confidential Core
.png)
Throughout this series, we've explored the fundamentals of confidential computing, remote attestation, and real-world implementations. As organizations evaluate their security strategies, the choice between different isolation approaches depends on their specific threat models and operational requirements. Whether you need the hardware-backed guarantees of confidential computing or the flexible, workload-focused protection of Edera Confidential Core – or potentially both – the key is understanding which threats you're defending against.
ICYMI, you can check out the full Confidential Computing series.

-3.png)