Announcing Edera for Containers 1.0 Now Generally Available
Today marks a significant milestone for our team at Edera. After less than a year of intense development, we're thrilled to announce that Edera for Containers has reached its 1.0 release – our first, generally available, production-ready solution that reimagines container infrastructure for the cloud native world.
When we founded Edera, we set out with an ambitious mission: to fix computing by resolving the inherent tension between platform velocity and security. We saw organizations struggling with a painful choice – move fast and accept security risks, or lock down their infrastructure and hinder innovation. We believed there had to be a better way.
The problem has been clear for years. As Kubernetes has become the default compute platform for modern organizations, it has also become an increasingly attractive target for attackers. Credential theft, living-off-the-land attacks, and container escapes have grown more prevalent, yet the fundamental architecture of containers was never designed with security as a first-class concern.
Unlike traditional container security solutions that focus on detection and monitoring, Edera for Containers uses “zones” to create strong isolation between containers by default, eliminating entire classes of threats at the architectural level. You can think of a zone as the next generation of a kubernetes sandbox (Figure 1). This means the burden of securing containers is no longer on the development teams, it's securely transparent from the start.
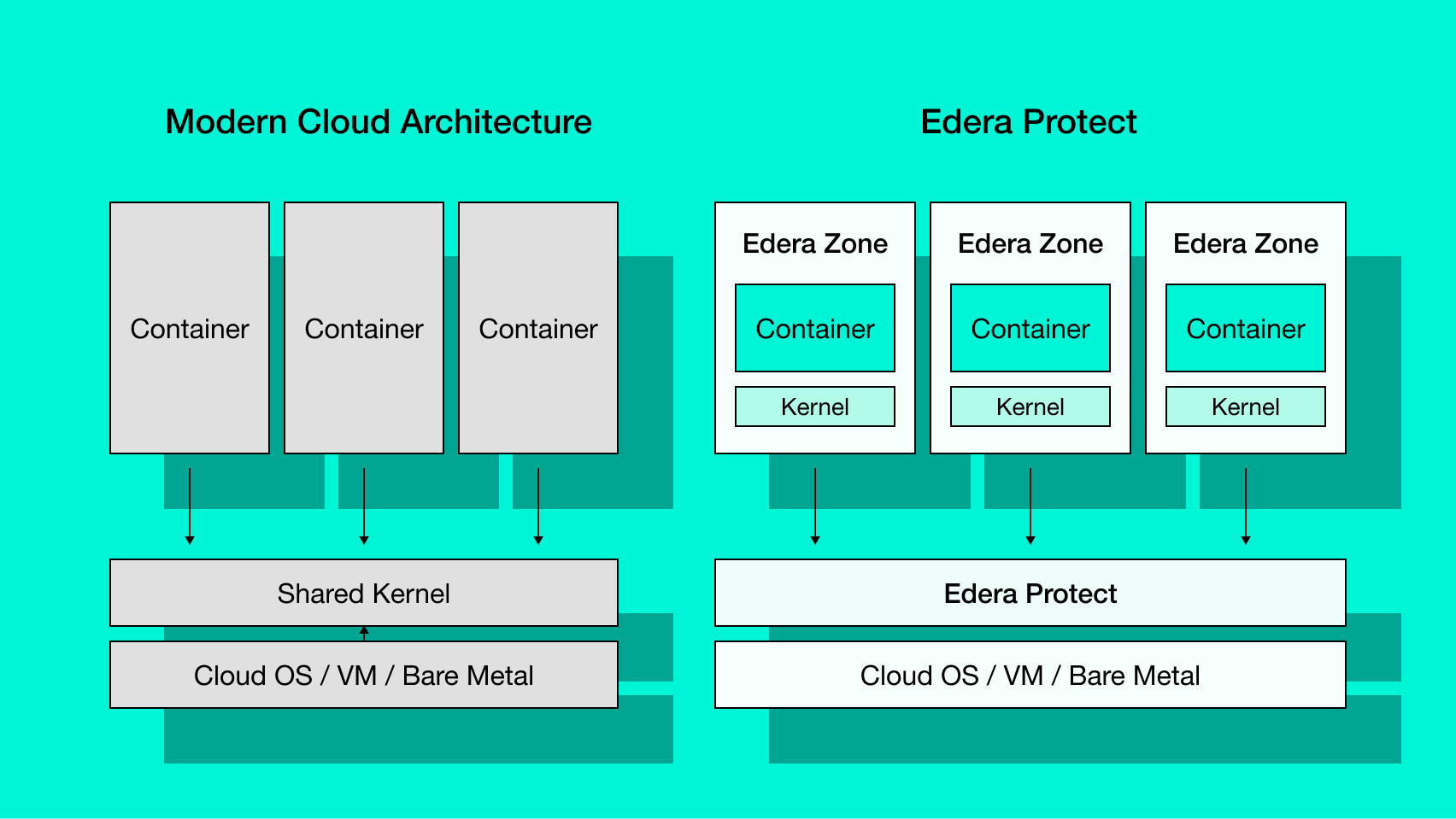
Edera holistically addresses container security by re-architecting the standard container runtime. Our approach provides full isolation between containers by default, while maintaining the performance and efficiency developers expect from modern cloud-native infrastructure. The journey to 1.0 has been intense, but the results speak for themselves.
In our benchmarks, Edera for Containers has achieved:
- Over 250 secure zones on a single Kubernetes node with just 64GB of RAM
- Memory Ballooning support via dynamic resource management. Pod memory begins at a configured target and can balloon up to a designated maximum dynamically.
- Container start times as fast as native Docker using our innovative "warm zones" technology
- Seamless integration with existing Kubernetes infrastructure deployed in minutes
- Scalable to tens of thousands of nodes
Edera for Containers plugs directly into existing Kubernetes infrastructure in minutes and scales to tens of thousands of nodes. This means you can dramatically improve the resource utilization and security posture of your cloud-native applications without disrupting your developers' workflows or requiring a complete infrastructure overhaul.
Our 1.0 release includes several key capabilities that our early users have found invaluable. We've expanded our security model to support running multiple containers inside a single Edera zone, giving teams more flexibility while maintaining strong security boundaries. We've also added support for fully isolated file system sharing between the host and zones, ensuring that sensitive data remains protected even when shared. Last but not least, we’d added support for dynamic resource management or container “memory ballooning”. In this mode, pod memory sits at a configured target and can balloon up to a maximum amount of memory dynamically.
For teams running on AWS, we've added full support for Amazon Linux 2023 in addition to existing support for Amazon Linux 2. We've integrated with the Cilium Container Network Interface, enabling advanced networking capabilities while maintaining our security guarantees. And for those who need deep visibility into their environments, we've built comprehensive observability features, including Prometheus metrics for zone memory consumption and health endpoints for all Edera components.
Looking ahead, we're already working on expanding Edera for Containers with support for defining security boundaries at the Kubernetes namespace layer and deeper integration with cloud provider security features. This 1.0 release is just the beginning of our journey to make truly secure containers the industry standard.
The future of secure, high-velocity cloud computing is here – and it's called Edera.
Our Commitment to Open Source
As we reach this milestone, we're not just announcing a product – we're also reinforcing our commitment to the open source community. Today, we're open sourcing Styrolite, our Linux container runtime built from scratch in Rust. Styrolite serves as the foundation for Edera and provides a programmatic interface for building and running sandboxed environments.
We built Styrolite because we needed a container runtime that could operate as a microservice within our platform, allowing us to run containers programmatically similar to how the Container Runtime Interface (CRI) enables Kubernetes to manage containers. But we immediately recognized that this technology could benefit the broader community. Any tool or platform requiring secure, sandboxed environments can leverage Styrolite's capabilities.
Open source is deeply embedded in our company DNA. From Alex Zenla's early contributions to Ubuntu when she was just 13 years old to her recent work rewriting portions of the Xen Hypervisor in Rust, and Ariadne Conill's significant contributions as an Alpine Linux maintainer and creator of Wolfi, our team has always been engaged in building technology that benefits everyone. That's why we've officially joined the Cloud Native Computing Foundation (CNCF) and The Linux Foundation.
We're committing to contribute something substantial to the open source community with every major Edera product release. We believe that the best way to address the challenges of open source security, licensing debates, and developer compensation is to focus on creating substance rather than noise.
Test Drive Edera for Containers at Kubecon EU
If you're heading to KubeCon + CloudNativeCon Europe in London this year, we'd love to connect. Our team will be demonstrating how Edera for Containers integrates seamlessly into existing Kubernetes environments while providing unprecedented security isolation. Reach out for a live demo and to discuss how we can help secure your specific infrastructure.

-3.png)